FIPS 140-2 密碼學模組標準簡介
依據NIST(National Institute Standards and Technology) 的定義, 密碼學模組可以是硬體元件或模組、軟體韌體程式或模組、或它們的組合
美國於1994年通過FIPS 140-1規範,並於2001年修正為FIPS 140-2。目前FIPS 140-2的規範是國際上業界所公認的密碼學模組標準
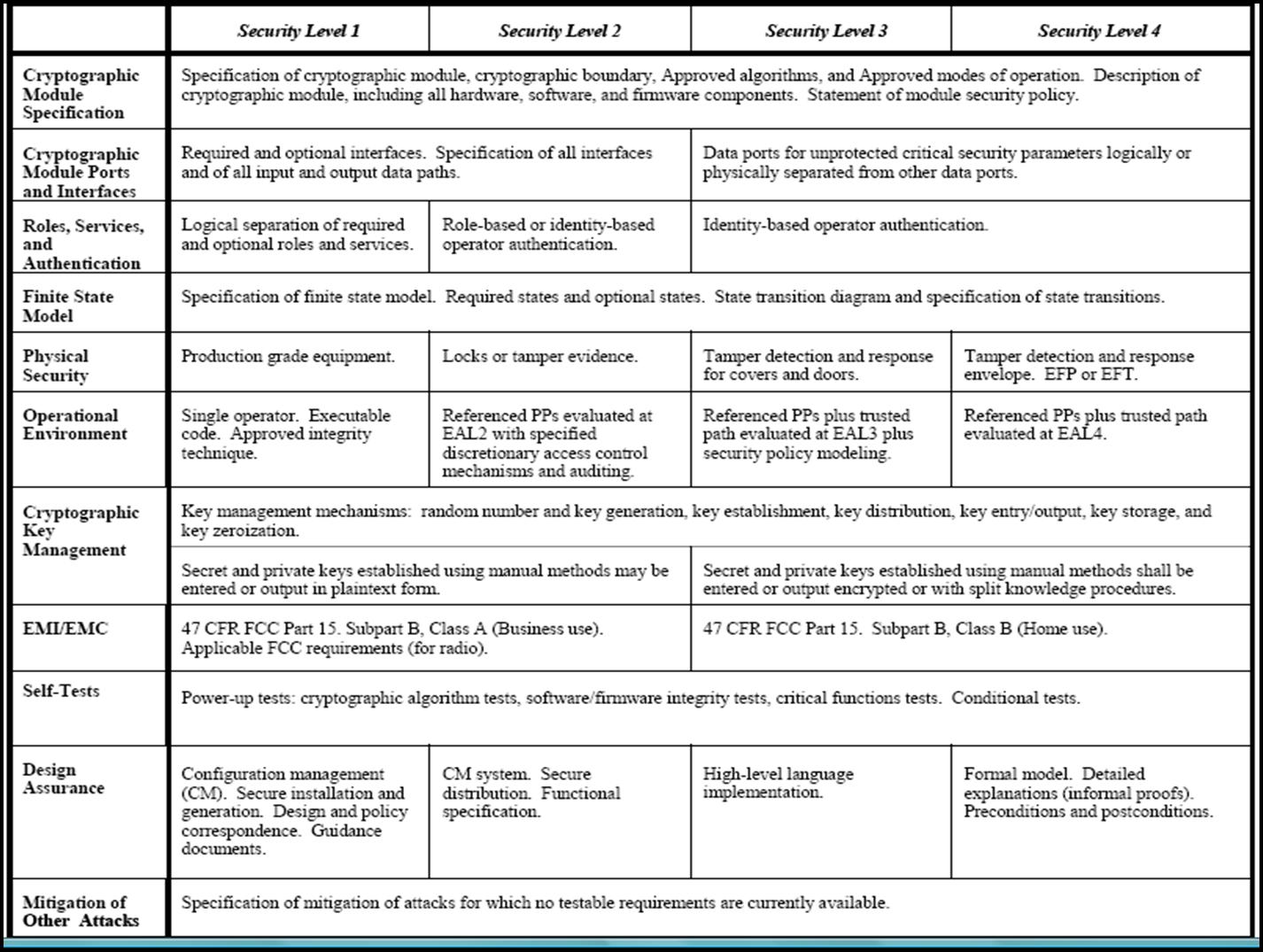
FIPS 140-2標準訂定密碼學模組的四種安全等級,從最低要求的第一級到最高階的第四級,每個安全等級各須滿足11個安全要件。每個安全等級的共同基本需求包括模組輸出入及控制與狀態介面的描述、至少須實現一個核定的密碼學演算法、模組啟動時自我測試密碼學演算法、模組安全政策的定義、授權角色與安全服務的說明、驗證機制的選擇、以及模組須以有限狀態機器描述等。
官方文件在這裡: http://csrc.nist.gov/publications/fips/fips140-2/fips1402.pdf
FIPS 140
- The Federal Information Processing Standard 140 (FIPS) are series of publications numbered 140 which are a U.S. government computer security standards that specify requirements for cryptography modules
- the current version of the standard is FIPS 140-2, issued on 25 May 2001.
Security level 1
- Basic security requirements are specified for a cryptographic module (e.g., at least one Approved algorithm or Approved security function shall be used)
- No specific physical security mechanisms are required
- Basic requirement for production-grade components
- Allows the software and firmware components of a cryptographic module to be executed on a general purpose computing system using an unevaluated operating system.
Security level 2
- Enhances the physical security mechanisms of a Security Level 1 cryptographic module by adding the requirement for tamper-evidence
Tamper-evident coatings or seals are placed on a cryptographic module so that the coating or seal must be broken to attain physical access to the plaintext cryptographic keys and critical security parameters (CSPs) within the module.
- Role-based authentication in which a cryptographic module authenticates the authorization of an operator to assume a specific role and perform a corresponding set of services.
Security level 3
- Adds requirements for physical tamper-resistance (making it difficult for attackers to gain access to sensitive information contained in the module)
The physical security mechanisms may include the use of strong enclosures and tamper detection/response circuitry that zeroizes all plaintext CSPs when the removable covers/doors of the cryptographic module are opened.
- Identity-based authentication mechanisms
A cryptographic module authenticates the identity of an operator and verifies that the identified operator is authorized to assume a specific role and perform a corresponding set of services
- The entry or output of plaintext CSPs be performed using ports that are physically separated from other ports, or interfaces that are logically separated using a trusted path from other interfaces
Plaintext CSPs may be entered into or output from the cryptographic module in encrypted form
Security level 4
- Makes the physical security requirements more stringent, and requires robustness against environmental attacks.
Penetration of the cryptographic module enclosure from any direction has a very high probability of being detected, resulting in the immediate zeroization of all plaintext CSPs
Against a security compromise due to environmental conditions or fluctuations outside of the module's normal operating ranges for voltage and temperature
- Level 4 cryptographic modules are useful for operation in physically unprotected environments.
Functional Security Objectives
- To employ and correctly implement the Approved security functions for the protection of sensitive information
- To protect a cryptographic module from unauthorized operation or use.
- To prevent the unauthorized disclosure of the contents of the cryptographic module, including plaintext cryptographic keys and CSPs.
- To prevent the unauthorized and undetected modification of the cryptographic module and cryptographic algorithms, including the unauthorized modification,substitution, insertion, and deletion of cryptographic keys and CSPs.
- To provide indications of the operational state of the cryptographic module.
- To ensure that the cryptographic module performs properly when operating in an Approved mode of operation.
- To detect errors in the operation of the cryptographic module and to prevent the compromise of sensitive data and CSPs resulting from these errors.
Scope of requirements
- Cryptographic module specification (what must be documented)
- Cryptographic module parts and interfaces (what information flows in and out, and how it must be segregated)
- Roles, services and authentication (who can do what with the module, and how this is checked)
- Finite state model (documentation of the high-level states the module can be in, and how transitions occur)
- Physical security (tamper evidence and resistance, and robustness against extreme environmental conditions)
- Operational environment (what sort of operating system the module uses and is used by)
- Cryptographic key management (generation, entry, output, storage and destruction of keys)
- EMI/EMC
- Self-tests (what must be tested and when, and what must be done if a test fails)
- Design assurance (what documentation must be provided to demonstrate that the module has been well designed and implemented)
- Mitigation of other attacks (if a module is designed to mitigate against, say, TEMPEST attacks then its documentation must say how)
參考資料:
網路安全: 理論與實務(第二版), 楊中皇著, http://crypto.nknu.edu.tw/Welcome.html (楊中皇老師的首頁)
FIPS 140-2 官方網站: http://csrc.nist.gov/publications/fips/fips140-2/fips1402.pdf
FIPS 140-2 認證廠商名單
玉山科技 版權所有 © Copyright AsiaPeak 2006, All Rights Reserved
|

